The FBI's Pursuit of DDoS Cyberattack Perpetrators
Tracing the Culprits: The FBI's Unwavering Hunt for DDoS Cyberattack Instigators
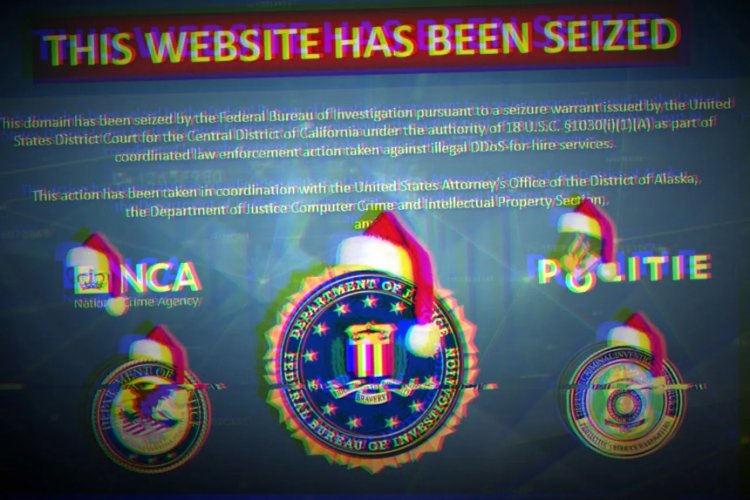
In 2016, a network of compromised internet-connected devices, including vulnerable security cameras and routers, orchestrated a massive distributed denial-of-service (DDoS) attack that temporarily took down prominent websites such as Twitter, Reddit, GitHub, and Spotify. This incident marked one of the most substantial DDoS attacks at that time and garnered attention from individuals less familiar with cybersecurity.
Although subsequent DDoS attacks haven't achieved the same level of notoriety, the issue persists. On December 15, 2022, just before Christmas—a historically popular period for launching DDoS attacks—the FBI disclosed its success in dismantling multiple websites offering booter or stresser services, which enable non-technical users to execute DDoS attacks at a low cost. In conjunction with this action, the FBI apprehended seven individuals believed to be running these illicit services. Further interventions occurred in May, with additional booter sites being shut down.
These recent operations, including the investigation into the Mirai malware responsible for the significant 2016 attacks, were spearheaded by the FBI office in Anchorage. Elliott Peterson, an FBI agent who played a pivotal role in these inquiries, shared insights at the Black Hat cybersecurity conference in Las Vegas alongside cybercrime prosecutor Cameron Schroeder. They discussed the intricacies of the investigations leading to the December and May takedowns.
Schroeder disclosed that Peterson himself designed the replacement pages for the seized websites. With a decade of focus on DDoS attacks, Peterson conversed with TechCrunch about his efforts to track down the culprits behind DDoS services and pinpoint which services to target. He detailed law enforcement's objectives in these investigations, the evolution of DDoS attacks, and the identities of the individuals behind them.
The conversation has been edited for clarity and conciseness.
TechCrunch: How extensive is your experience in investigating DDoS attacks, and how have these attacks transformed over the years?
Peterson: I've been engaged in investigating DDoS attacks for around nine or ten years. The landscape has evolved significantly during this period. Initially, our focus centered on the primary booter or stresser services—the heart of the market and user base. However, while probing these services, we delved into the realm of botnets, leading to a back-and-forth between addressing different segments of the DDoS landscape. Criminals react to our actions, prompting us to adjust and learn continuously over the years.
TechCrunch: What stands out as the most significant change in the last decade?
Peterson: The expansion of our partnerships stands out. When we began, collaboration within the security community focused on DDoS was limited. Yet, over time, we have witnessed greater engagement from the private sector, academia, and law enforcement—more entities genuinely interested in combating this issue. While there's sometimes a perception that DDoS is a solved or unexciting problem, the reality is more nuanced. Temporary DDoS attacks create challenges during the attack but often fade from memory afterward. However, larger-scale attacks pose persistent threats and demand substantial mitigation efforts.
TechCrunch: What about the financial impact of DDoS attacks?
Peterson: Assessing financial losses related to DDoS attacks proves challenging. While some cases involve extortion or victim payments, indirect costs complicate calculations. Continuous DDoS attacks can lead victims to invest in additional bandwidth to counteract attackers, driving up expenses. The magnitude of losses is difficult to quantify accurately. Notably, DDoS mitigation companies like Cloudflare, Akamai, and Fastly demonstrate the scope of the problem, with ISPs also adjusting plans to accommodate DDoS threats.
TechCrunch: How do you select targets for investigation among the vast landscape of DDoS attacks?
Peterson: Our ability to choose targets is a significant advantage. We prioritize top services—those responsible for the most frequent attacks, with extensive customer bases and capabilities for major assaults. We employ a similar methodology for botnets, with notable entities attracting our attention. For instance, Mirai was a case handled entirely by the FBI Anchorage office, exemplifying the dynamic nature of DDoS threats and the need for adaptable responses.
Schroeder: To add to that, Mirai showcases the shifting perception of DDoS importance. When a substantial botnet like Mirai emerges, the significance of DDoS becomes evident, contrary to those who dismiss it as inconsequential.
The conversation covers multiple facets of DDoS attacks and their investigation, highlighting the evolution of the threat landscape and the proactive measures taken by law enforcement to combat these cyber threats.

 chandni
chandni 



